[Implemented] Two Factor Authentication (2FA)
-
I actually wanted to answer this topic: https://vulndetect.org/topic/344/data-processing-policy, but wasn't able to. Probably because this thread is somehow in Announcements!?
Anyway, my answer: I really don't like this architecture. From a security point of view, it is extremely valuable data to have a list of security vulnerabilities of a (or better said: of MANY) concrete targets. It would be way more secure to have all the data stay on the clients.
Anyway, since I don't know a good alternative, I'll stay with VulnDetect for now. In order to protect my account as good as possible, I would like to see two factor authentication being implemented to the website. Shouldn't be a big issue since libraries for HOTP/TOTP are publicly available.
Thanks!
-
A Two Factor Authentication is really a cool idea, thank you for suggesting this!
I linked it in the Overview of Feature and Functionality Requests. -
@Tom
You store very sensitive data (the complete list of application that a user has installed).
Families will have the option to store multiple computers in one account.
And business users also have multiple computers and here a leak of information could be critical.So please implement Two Factor Authentication (2FA) by allowing users to log on with a Temporal One Time Password (TOTP).
And please don't forget to add 2FA Recovery Codes (codes that users get when they set up 2FA and that can be used instead of 2FA).
-
One very important annotation to this feature:
Besides to the QR-Code many services offer the Two-Factor-Token also as plain text (the part behind secret=) that can be copied to the clipboard and then inserted in any Two Factor App on the Desktop.
I am using KeePassXC and this client can also generate 2FA keys for the two-factor-authentication.
I am lucky that many services like GitHub, Google and Paypal (just some examples) offer the Two-Factor-Token as plain text.Otherwise I have to use a QR-Code scanner on my phone, scan this code, send me the code from my phone to myself, open the mail app, copy the code (the part behind secret=) and paste it in KeePassXC.
Showing the Two-Factor-Token makes it much easier for me (and also other users). -
I found a small issue in the 2FA login:
The field where I enter the 2FA code is not named properly, so password managers can not fill this fields.I am using KeePassXC and this password manager does not only fill the username and password into login fields (if the URL matches), it also fills the 2FA code in the login form.
KeePassXC can generate the 2FA codes.Normally I see in the field where I have to enter the 2FA code a green icon on the right:
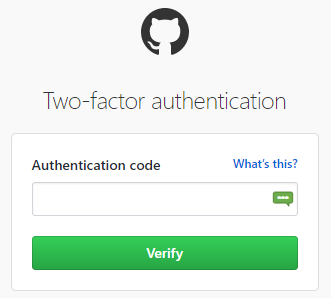
I just click this icon and KeePassXC fills the 2FA code.
At VulnDetect this icon is missing:
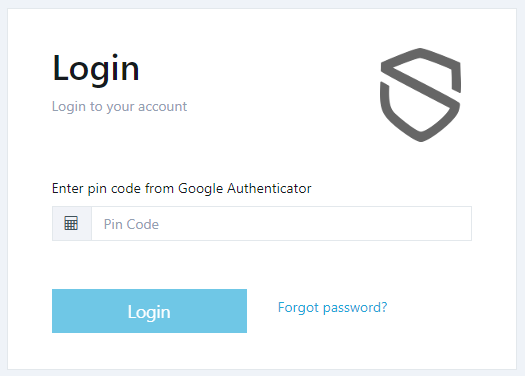
So here I have to switch to KeePassXC, search for the entry "VulnDetect", select the entry in the search results, manually copy the 2FA code and paste it in the field.
The fix is very easy and described here:
https://github.com/keepassxreboot/keepassxc-browser/issues/826So please fix this, all users using password managers will benefit from it.
-
@Tom When will this little issue be fixed?
It is very annoying, because I delete the browser cache very often and then I have to manually search the entry in KeePassXC and manually copy and paste the 2FA code.
And I reported this issue 4 months ago! -
@OLLI_S I'm not much into the details of the two factor authentication. But I will push for a review of it.
However, during the rest of July and the first half of August we have a development freeze, which means that we will only fix critical bugs, due to vacations. The earliest this will be handled is in late August.
-
It is a very small change:
One programmer of KeePassCX suggests:Yes, adding
name="2fa"would be enough. However, I'd suggest usingautocomplete="one-time-code" -
In the business UI 2FA (Two Factor Authentication) is working:
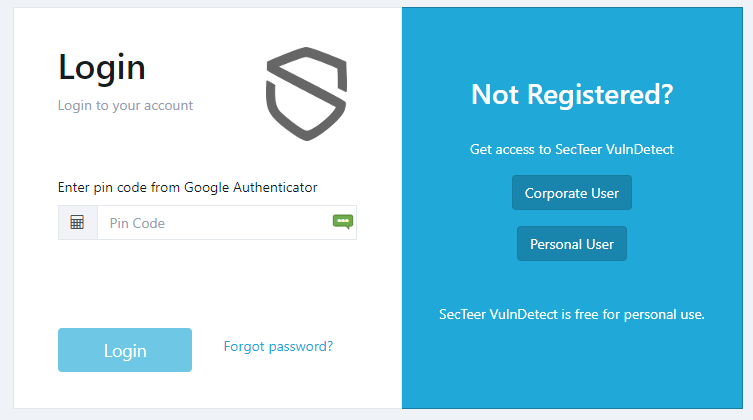
The icon in the 2FA field is from KeePassXC.
@Tom Should I mark the issue as Implemented?
-
@OLLI_S Yes, this is implemented
-
T Tom referenced this topic on